High Sierra Security Update 2019 004 For Mac 2012
About Apple security updates
Jul 24, 2019 Apple has now released fixed versions of the two Security Updates - see this article for full details. Apple has pulled the High Sierra and Sierra Security Updates 2019-004 today as a result of numerous users suffering problems when their updated Macs go to sleep. These have been reported particularly in recent MacBook Pro models. Announced last year, Apple’s new File System (APFS) will be the default as of macOS High Sierra on the Mac. IOS devices have been running the new file system since iOS 10.3, and Apple has finally introduced it to the Mac. Designed to make the best use of Flash technology (Solid State), it brings faster performance and better security.
For our customers' protection, Apple doesn't disclose, discuss, or confirm security issues until an investigation has occurred and patches or releases are available. Recent releases are listed on the Apple security updates page.
Apple security documents reference vulnerabilities by CVE-ID when possible.
For more information about security, see the Apple Product Security page.
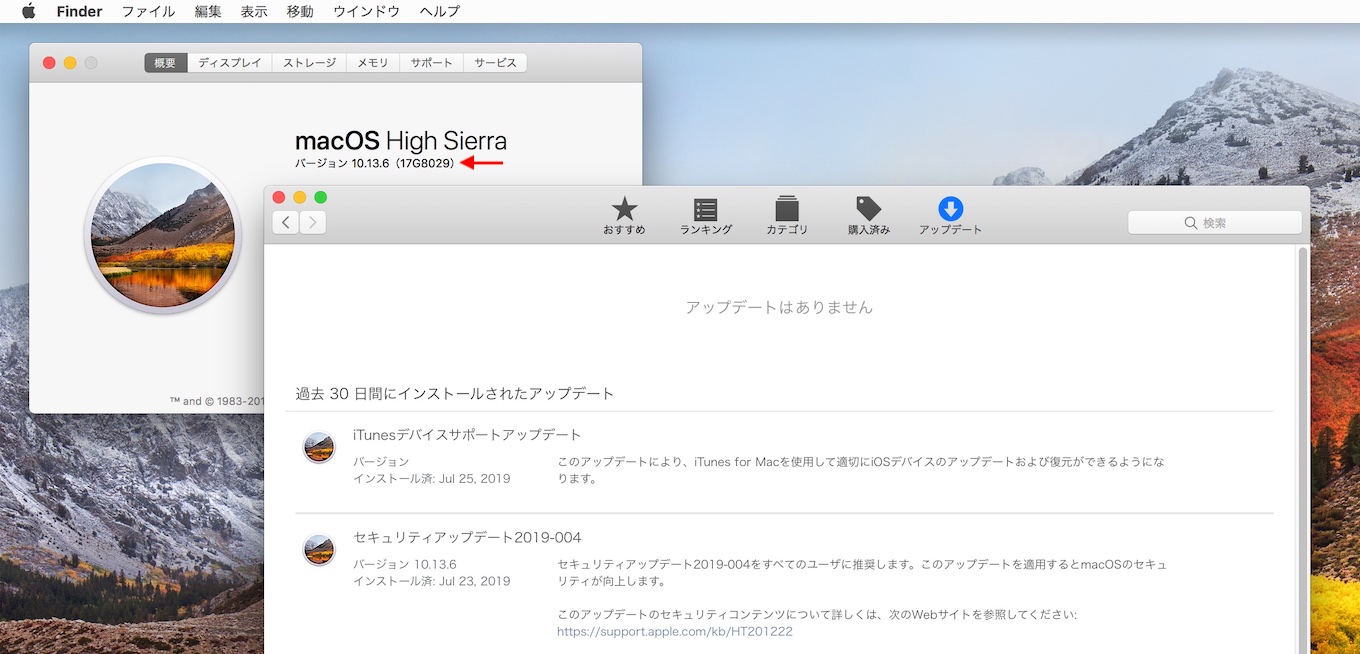
macOS Mojave 10.14.6, Security Update 2019-004 High Sierra, Security Update 2019-004 Sierra
Released July 22, 2019
AppleGraphicsControl
Available for: macOS Mojave 10.14.5
Impact: An application may be able to read restricted memory
Description: A validation issue was addressed with improved input sanitization.
CVE-2019-8693: Arash Tohidi of Solita
autofs
Available for: macOS Sierra 10.12.6, macOS Mojave 10.14.5, macOS High Sierra 10.13.6
Impact: Extracting a zip file containing a symbolic link to an endpoint in an NFS mount that is attacker controlled may bypass Gatekeeper
Description: This was addressed with additional checks by Gatekeeper on files mounted through a network share.
High Sierra Security Update
CVE-2019-8656: Filippo Cavallarin
Bluetooth
Available for: macOS Sierra 10.12.6, macOS High Sierra 10.13.6, macOS Mojave 10.14.5
Impact: A remote attacker may be able to cause arbitrary code execution
Description: A memory corruption issue was addressed with improved input validation.
CVE-2018-19860
Bluetooth

Available for: macOS Sierra 10.12.6, macOS Mojave 10.14.5, macOS High Sierra 10.13.6
Impact: An attacker in a privileged network position may be able to intercept Bluetooth traffic (Key Negotiation of Bluetooth - KNOB)
Description: An input validation issue existed in Bluetooth. This issue was addressed with improved input validation.
CVE-2019-9506: Daniele Antonioli of SUTD, Singapore, Dr. Nils Ole Tippenhauer of CISPA, Germany, and Prof. Kasper Rasmussen of University of Oxford, England
The changes for this issue mitigate CVE-2020-10135.
Entry added August 13, 2019, updated June 25, 2020
Carbon Core
Available for: macOS Mojave 10.14.5
Impact: A remote attacker may be able to cause arbitrary code execution
Description: A use after free issue was addressed with improved memory management.
CVE-2019-8661: Natalie Silvanovich of Google Project Zero
Core Data
Available for: macOS Mojave 10.14.5
Impact: A remote attacker may be able to leak memory
Xml notepad for mac os x. Description: An out-of-bounds read was addressed with improved input validation.
CVE-2019-8646: Natalie Silvanovich of Google Project Zero
Core Data
Available for: macOS Mojave 10.14.5
Impact: A remote attacker may be able to cause unexpected application termination or arbitrary code execution
Description: A memory corruption issue was addressed with improved input validation.
CVE-2019-8660: Samuel Groß and Natalie Silvanovich of Google Project Zero
CUPS
Available for: macOS Sierra 10.12.6, macOS Mojave 10.14.5, macOS High Sierra 10.13.6
Impact: An attacker in a privileged network position may be able to execute arbitrary code
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2019-8675: Stephan Zeisberg (github.com/stze) of Security Research Labs (srlabs.de)
CVE-2019-8696: Stephan Zeisberg (github.com/stze) of Security Research Labs (srlabs.de)
It guards your Mac, network, online activities and your identity with innovative detection technologies optimized to combat todays aggressive, rapid-fire attacks. Norton Security for Mac delivers the fastest and lightest available. How to remove symantec mac.
Entry added August 14, 2019, updated September 17, 2019
Disk Management
Available for: macOS Mojave 10.14.5
Impact: A malicious application may be able to execute arbitrary code with system privileges
Description: A memory initialization issue was addressed with improved memory handling.
CVE-2019-8539: ccpwd working with Trend Micro's Zero Day Initiative
Entry added September 17, 2019
Disk Management
Available for: macOS Mojave 10.14.5
Impact: An application may be able to execute arbitrary code with system privileges
Mac Os High Sierra Security Update
Description: A memory corruption issue was addressed with improved memory handling.
CVE-2019-8697: ccpwd working with Trend Micro’s Zero Day Initiative
FaceTime
Available for: macOS Mojave 10.14.5
Impact: A remote attacker may be able to cause arbitrary code execution
Description: A memory corruption issue was addressed with improved input validation.
CVE-2019-8648: Tao Huang and Tielei Wang of Team Pangu
Found in Apps
Available for: macOS Mojave 10.14.5
Impact: A remote attacker may be able to leak memory
Description: This issue was addressed with improved checks.
CVE-2019-8663: Natalie Silvanovich of Google Project Zero
Game Center
Available for: macOS Mojave 10.14.5
Impact: A local user may be able to read a persistent account identifier
Description: This issue was addressed with a new entitlement.
CVE-2019-8702: Min (Spark) Zheng and Xiaolong Bai of Alibaba Inc.
Entry added February 24, 2020
Grapher
Available for: macOS Mojave 10.14.5
Impact: An application may be able to execute arbitrary code with system privileges
Description: A memory corruption issue was addressed with improved memory handling.
CVE-2019-8695: riusksk of VulWar Corp working with Trend Micro's Zero Day Initiative
Graphics Drivers
Available for: macOS Mojave 10.14.5, macOS High Sierra 10.13.6
Impact: An application may be able to read restricted memory
Description: A validation issue was addressed with improved input sanitization.
CVE-2019-8691: Aleksandr Tarasikov (@astarasikov), Arash Tohidi of Solita, Lilang Wu and Moony Li of Trend Micro's Mobile Security Research Team working with Trend Micro's Zero Day Initiative
CVE-2019-8692: Lilang Wu and Moony Li of Trend Micro Mobile Security Research Team working with Trend Micro's Zero Day Initiative
Entry updated July 25, 2019
Heimdal
Available for: macOS Sierra 10.12.6, macOS High Sierra 10.13.6, macOS Mojave 10.14.5
Impact: An issue existed in Samba that may allow attackers to perform unauthorized actions by intercepting communications between services
Description: This issue was addressed with improved checks to prevent unauthorized actions.
CVE-2018-16860: Isaac Boukris and Andrew Bartlett of the Samba Team and Catalyst
IOAcceleratorFamily
Available for: macOS Mojave 10.14.5
Impact: An application may be able to execute arbitrary code with kernel privileges
Description: A memory corruption issue was addressed with improved memory handling.
CVE-2019-8694: Arash Tohidi of Solita
libxslt
Available for: macOS Sierra 10.12.6, macOS High Sierra 10.13.6, macOS Mojave 10.14.5
Impact: A remote attacker may be able to view sensitive information
Description: A stack overflow was addressed with improved input validation.
CVE-2019-13118: found by OSS-Fuzz
Quick Look
Available for: macOS Sierra 10.12.6, macOS High Sierra 10.13.6, macOS Mojave 10.14.5
Impact: An attacker may be able to trigger a use-after-free in an application deserializing an untrusted NSDictionary
Description: This issue was addressed with improved checks.
CVE-2019-8662: Natalie Silvanovich and Samuel Groß of Google Project Zero
Safari
Available for: macOS Mojave 10.14.5
Impact: Visiting a malicious website may lead to address bar spoofing
Description: An inconsistent user interface issue was addressed with improved state management.
CVE-2019-8670: Tsubasa FUJII (@reinforchu)
Security
Available for: macOS Sierra 10.12.6, macOS High Sierra 10.13.6
Impact: An application may be able to execute arbitrary code with system privileges
Description: A memory corruption issue was addressed with improved memory handling.
CVE-2019-8697: ccpwd working with Trend Micro’s Zero Day Initiative
sips
Available for: macOS Sierra 10.12.6, macOS High Sierra 10.13.6
Impact: An application may be able to execute arbitrary code with system privileges
Description: A memory corruption issue was addressed with improved memory handling.
CVE-2019-8701: Simon Huang(@HuangShaomang), Rong Fan(@fanrong1992) and pjf of IceSword Lab of Qihoo 360
Entry added October 8, 2019
Siri
Available for: macOS Mojave 10.14.5
Impact: A remote attacker may be able to leak memory
Description: An out-of-bounds read was addressed with improved input validation.
CVE-2019-8646: Natalie Silvanovich of Google Project Zero
Time Machine
Available for: macOS Mojave 10.14.5
Impact: The encryption status of a Time Machine backup may be incorrect
Description: An inconsistent user interface issue was addressed with improved state management.
CVE-2019-8667: Roland Kletzing of cyber:con GmbH
UIFoundation
Available for: macOS Sierra 10.12.6, macOS High Sierra 10.13.6, macOS Mojave 10.14.5
Impact: Parsing a maliciously crafted office document may lead to an unexpected application termination or arbitrary code execution
Description: An out-of-bounds read was addressed with improved input validation.
CVE-2019-8657: riusksk of VulWar Corp working with Trend Micro's Zero Day Initiative
WebKit
Available for: macOS Mojave 10.14.5
Impact: Processing maliciously crafted web content may lead to universal cross site scripting
Description: A logic issue existed in the handling of document loads. This issue was addressed with improved state management.
CVE-2019-8690: Sergei Glazunov of Google Project Zero
WebKit
Available for: macOS Mojave 10.14.5
Impact: Processing maliciously crafted web content may lead to universal cross site scripting
Description: A logic issue existed in the handling of synchronous page loads. This issue was addressed with improved state management.
CVE-2019-8649: Sergei Glazunov of Google Project Zero
WebKit
Available for: macOS Mojave 10.14.5
Impact: Processing maliciously crafted web content may lead to universal cross site scripting
Description: A logic issue was addressed with improved state management.
CVE-2019-8658: akayn working with Trend Micro's Zero Day Initiative
WebKit
Available for: macOS Mojave 10.14.5
Impact: Processing maliciously crafted web content may lead to arbitrary code execution
Description: Multiple memory corruption issues were addressed with improved memory handling.
CVE-2019-8644: G. Geshev working with Trend Micro's Zero Day Initiative
CVE-2019-8666: Zongming Wang (王宗明) and Zhe Jin (金哲) from Chengdu Security Response Center of Qihoo 360 Technology Co. Ltd.
CVE-2019-8669: akayn working with Trend Micro's Zero Day Initiative
CVE-2019-8671: Apple
CVE-2019-8672: Samuel Groß of Google Project Zero
CVE-2019-8673: Soyeon Park and Wen Xu of SSLab at Georgia Tech
CVE-2019-8676: Soyeon Park and Wen Xu of SSLab at Georgia Tech
CVE-2019-8677: Jihui Lu of Tencent KeenLab
CVE-2019-8678: an anonymous researcher, Anthony Lai (@darkfloyd1014) of Knownsec, Ken Wong (@wwkenwong) of VXRL, Jeonghoon Shin (@singi21a) of Theori, Johnny Yu (@straight_blast) of VX Browser Exploitation Group, Chris Chan (@dr4g0nfl4me) of VX Browser Exploitation Group, Phil Mok (@shadyhamsters) of VX Browser Exploitation Group, Alan Ho (@alan_h0) of Knownsec, Byron Wai of VX Browser Exploitation
CVE-2019-8679: Jihui Lu of Tencent KeenLab
CVE-2019-8680: Jihui Lu of Tencent KeenLab
CVE-2019-8681: G. Geshev working with Trend Micro Zero Day Initiative
CVE-2019-8683: lokihardt of Google Project Zero
CVE-2019-8684: lokihardt of Google Project Zero
CVE-2019-8685: akayn, Dongzhuo Zhao working with ADLab of Venustech, Ken Wong (@wwkenwong) of VXRL, Anthony Lai (@darkfloyd1014) of VXRL, and Eric Lung (@Khlung1) of VXRL
CVE-2019-8686: G. Geshev working with Trend Micro's Zero Day Initiative
CVE-2019-8687: Apple
CVE-2019-8688: Insu Yun of SSLab at Georgia Tech
CVE-2019-8689: lokihardt of Google Project Zero
Additional recognition
Classroom
We would like to acknowledge Jeff Johnson of underpassapp.com for their assistance.
Game Center
We would like to acknowledge Min (Spark) Zheng and Xiaolong Bai of Alibaba Inc. for their assistance.
Installing security updates is one of the best ways to protect your Mac against online attacks. Apple regularly releases security patches for various macOS versions to fix known vulnerabilities.
Last May 13, Apple released Security Update 2019-003 for Sierra and High Sierra, together with the macOS Mojave 10.14.5 update. The macOS Mojave 10.14.5 update is around 2.8 GB, while Security Update 2019-003 is 1.9 GB in size. These updates were released to address vulnerabilities in various products. Safari 12.1.1 was also included in this security update.
Here are some of the changes High Sierra Security Update 2019-003 brings:
- AirPlay 2 support for compatible Smart TVs
- Improvements to the Apple News+ app
- Lower audio latency for MacBook Pro 2018
- Fixed a bug in OmniOutliner and OmniPlan
- Disabling of accessories using unsecured Bluetooth connections
- Fixed an issue with a user account password reset after using a personal recovery key (PRK) in FileVault
- Fixed an App Firewall bug
- Fixed a bypass for Gatekeeper checks
- Fixed vulnerabilities related to crafted audio and video files
- Fixed issues with Disk Images
- Fixed authentication issues with EFI
- Fixed three kernel bugs
- Fixed four SQLite bugs
- Fixed multiple bugs in WebKit
High Sierra users can download the security update via the App Store or get the standalone installer here.
The installation should be a straightforward process, but several users reported issues with High Sierra Security Update 2019-003. According to the reports, Security Update 2019-003 is causing problems on Mac — from slow bootup to crashing apps to install failures.
Other users had to install the update multiple times because the security features were not applied. In a case like theirs, the installation seems successful and the user is prompted to reboot, but then the user is prompted to install the update again after the restart. Some users can’t even boot at all.
The issues are different for each user, but the common denominator is that these problems started right after they installed the new High Sierra update. This problem has caused a lot of frustration among Mac users who installed the update, but Apple has yet to comment on the issue. There is a chance that this security update for High Sierra that is causing issues might be buggy so we’ll have to wait for Apple to acknowledge it.
Reasons Why Security Update 2019-003 Is Causing Problems on Mac
Security updates causing various issues on Mac are not a new thing. These issues with High Sierra Security Update 2019-003 can be caused by a lot of factors. Here are some of the possible reasons why you’re experiencing problems after installing the update:
- Failed or incomplete update installation
- Wonky third-party apps
- Not enough storage space
- Hard disk problems
- Virus or malware infection
We’ve listed down some troubleshooting methods below to fix these issues after installing the security update. This guide includes general troubleshooting steps and some problem-specific fixes. Depending on the problem you are having, you might need to try a combination of these solutions to see which one would work.
How to Fix Problems Caused by High Sierra Security Update 2019-003
Before you start, it is always advisable to run some maintenance steps to prepare your Mac for the troubleshooting process. Run your antivirus software to check if you have malicious software running on your computer. Delete all infected files to make sure you get rid of the virus or malware completely.
Delete apps and files that you no longer need and use Tweakbit MacRepair to get rid of junk files. After cleaning up your computer, restart it and try the methods below one by one.
Step 1: Run Apple Diagnostics or Apple Hardware Test
This diagnostic tool is built into every macOS device to check for issues with your hardware. For Macs released from 2013 or later, the tool is named Apple Diagnostics, while older Macs have the Apple Hardware Test. You need to run this utility to rule out any hardware problems.
To run Apple Diagnostics:
- Restart your Mac, then press and hold the D button while starting up.
- Apple Diagnostics will start automatically and scan your computer for problems.
- Once the process has been completed, you’ll be provided with a list of problems detected.
If you see a major problem during your scan, seek out Apple Support or send your Mac to a repair center to get it fixed. If there are no issues, proceed with the other fixes below.
Step 2: Reset NVRAM
Your Mac’s NVRAM stores information even when the power is turned off so that you don’t have to fetch it again when you resume computer use. However, some data could get corrupted during the update process and cause issues for your Mac. Resetting the NVRAM should easily fix this.
To reset NVRAM, restart your Mac and hold down Command + Option + P + R. Your computer should restart again after the NVRAM has been reset. After rebooting, check if the issues caused by the security update have been fixed.
Step 3: Check Storage Space
Another reason your update is failing and causing issues on your Mac is because of insufficient storage space. The High Sierra security update 2019-003 is a big file, so make sure you have enough room for it. Tech experts recommend clearing up at least 10 GB of space every time you install updates to avoid problems. Deleting your unused apps and junk files should clear up enough space for your updates.
Step 4: Install in Safe Mode
If you’re having problems booting up in normal mode, you can boot into Safe Mode instead. Just hold the Shift key when your computer is booting up to launch Safe Mode. Open the Mac App Store and install the High Sierra security update 2019-003 from there. Reboot into normal mode and see if the issues still persist.
Step 5: Reinstall macOS
If the update-related problems don’t go away after doing all the steps above, your last option is to reinstall macOS. Don’t worry because you can do this without wiping out your data. Reinstalling your computer’s operating system will overwrite all Apple system files and replace any problematic ones that may be causing your computer issues.
To reinstall macOS using Recovery Mode:
- Hold down Command + R while restarting your Mac.
- When the macOS Utilities window appears, click Reinstall macOS.
- Click Continue.
- Follow the onscreen instructions to choose the hard drive you want to install macOS on and start the installation.
Wait for the installation to be completed, then check if the previous issues still remain.
Summary
Installing security updates, such as 2019-003, is crucial in protecting your Mac against attacks because they fix bugs and vulnerabilities that could be exploited by attackers. If installing this security update for High Sierra is causing issues for your Mac, you can follow the guide above to resolve these issues while keeping your macOS updated.